|
4 | 4 | [](https://pypi.org/project/route-detect/) |
5 | 5 | [](https://pypi.org/project/route-detect/) |
6 | 6 |
|
7 | | -Find authentication (authn) and authorization (authz) security bugs in web application routes. |
| 7 | +Find authentication (authn) and authorization (authz) security bugs in web application routes: |
| 8 | + |
| 9 | +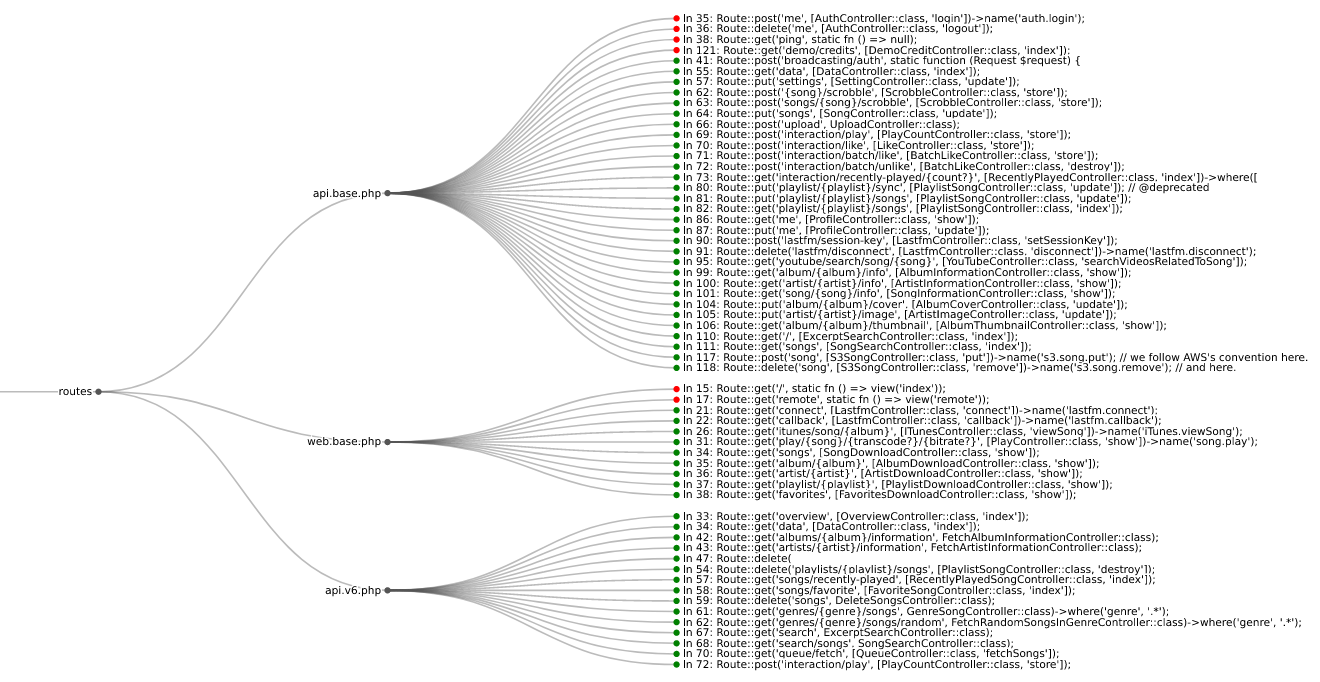 |
| 10 | + |
| 11 | +<p align="center"> |
| 12 | + <i>Routes from <code><a href="https://github.com/koel/koel">koel<a></code> streaming server</i> |
| 13 | +</p> |
8 | 14 |
|
9 | 15 | Web application HTTP route authn and authz bugs are some of the most common security issues found today. These industry standard resources highlight the severity of the issue: |
10 | 16 |
|
11 | 17 | - 2021 OWASP Top 10 #1 - [Broken Access Control](https://owasp.org/Top10/A01_2021-Broken_Access_Control/) |
12 | 18 | - 2021 OWASP Top 10 #7 - [Identification and Authentication Failures](https://owasp.org/Top10/A07_2021-Identification_and_Authentication_Failures/) (formerly Broken Authentication) |
13 | | -- 2019 OWASP API Top 10 #2 - [Broken User Authentication](https://github.com/OWASP/API-Security/blob/master/2019/en/src/0xa2-broken-user-authentication.md) |
14 | | -- 2019 OWASP API Top 10 #5 - [Broken Function Level Authorization](https://github.com/OWASP/API-Security/blob/master/2019/en/src/0xa5-broken-function-level-authorization.md) |
| 19 | +- 2023 OWASP API Top 10 #1 - [Broken Object Level Authorization](https://owasp.org/API-Security/editions/2023/en/0xa1-broken-object-level-authorization/) |
| 20 | +- 2023 OWASP API Top 10 #2 - [Broken Authentication](https://owasp.org/API-Security/editions/2023/en/0xa2-broken-authentication/) |
| 21 | +- 2023 OWASP API Top 10 #5 - [Broken Function Level Authorization](https://owasp.org/API-Security/editions/2023/en/0xa5-broken-function-level-authorization/) |
15 | 22 | - 2023 CWE Top 25 #11 - [CWE-862: Missing Authorization](https://cwe.mitre.org/top25/archive/2023/2023_top25_list.html) |
16 | 23 | - 2023 CWE Top 25 #13 - [CWE-287: Improper Authentication](https://cwe.mitre.org/top25/archive/2023/2023_top25_list.html) |
17 | 24 | - 2023 CWE Top 25 #20 - [CWE-306: Missing Authentication for Critical Function](https://cwe.mitre.org/top25/archive/2023/2023_top25_list.html) |
18 | 25 | - 2023 CWE Top 25 #24 - [CWE-863: Incorrect Authorization](https://cwe.mitre.org/top25/archive/2023/2023_top25_list.html) |
19 | 26 |
|
20 | | - |
21 | | - |
22 | | -<p align="center"> |
23 | | - <i>Routes from <code><a href="https://github.com/koel/koel">koel<a></code> streaming server</i> |
24 | | -</p> |
25 | | - |
26 | 27 | Supported web frameworks (`route-detect` IDs in parentheses): |
27 | 28 |
|
28 | 29 | - Python: Django (`django`, `django-rest-framework`), Flask (`flask`), Sanic (`sanic`) |
|
0 commit comments